My email gets bombarded by viruses, phishing scams, hoaxes and malware on almost a daily basis. A majority of the time, my anti-virus software catches and quarantines them and most of these malicious files are Windows related (but Mac viruses are on the rise too). But in this particular case, I received an “innocent” looking email which had “Re: hightechdad.com contract” as the subject. It was, luckily, put into my Gmail spam folder but since I frequently have contracts with various companies, I thought perhaps it was legit. Long story short, it wasn’t. It contained a malicious Word macro appropriately named “hightechdad.com_contract.doc”. I didn’t get infected though. I decided to investigate and analyze it instead. And, I wanted to pass on a warning to others.
There were several things that raised my concern about this:
- Gmail automatically put it into my Spam folder
- I did not know the sender
- Trying to preview the attachment revealed no details on a “contract”
- The preview said I had to both enable Editing AND enable Content
And there were items that almost faked me out:
- The subject had my domain in it
- The attachment had my domain in it
- The email itself looked somewhat legitimate
- The company sender in the email actually exists
So I decided to carefully step into analyzing this seemingly legitimate Word document.
This is what the email looked like.
It simply stated: “I have attached our contract. Please check it and let me know if you want to add any changes.” The writing was fine. In many cases with phishing scams, the grammar or punctuation is incorrect. In this case, it wasn’t.
There was a signature line. You can see it in the image above but this could be easily changed and may vary with other cases of this malware. And the signature matched the supposed sender’s domain. That all looked ok.
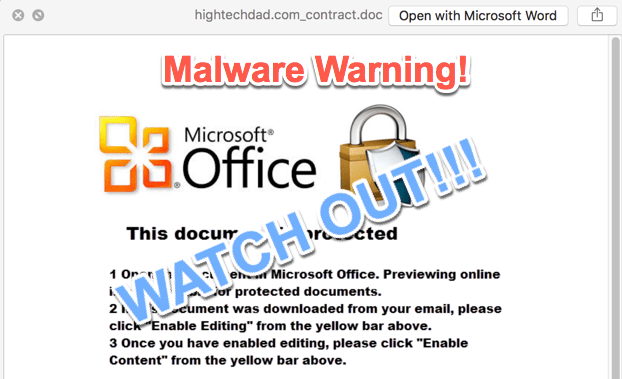
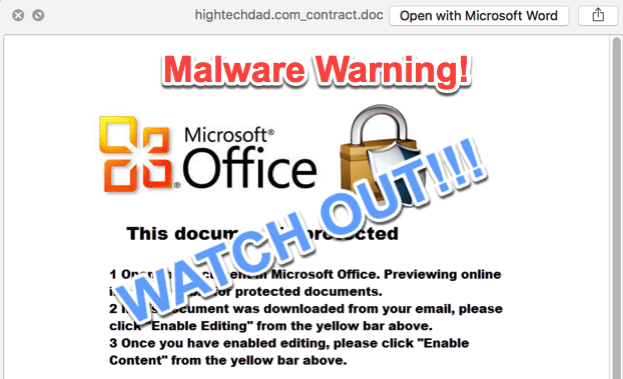
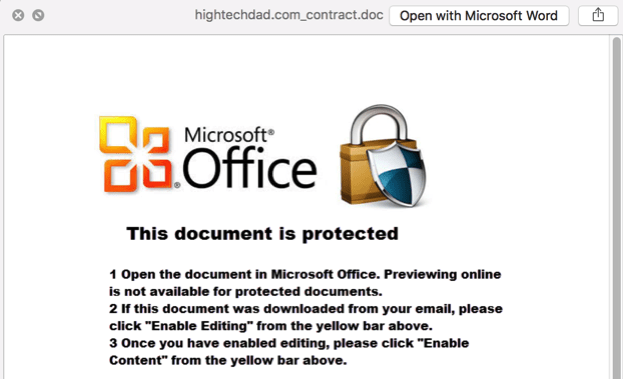
One way to possibly prevent Word macros from executing (and I am talking about on a Mac here) is to preview the document. If you save the document to your hard drive, you can click on it and then hit the Spacebar. This will usually bring up a preview. When I did that, this is what I saw.
It did bring up a preview of the content of the file but not of the malicious Word macro. It said:
- Open the document in Microsoft Office. Previewing online is not available for protected documents.
- If this document was downloaded from your email, please click “Enable Editing” from the yellow bar above.
- Once you have enabled editing, please click “Enable Content” from the yellow bar above.
Hmm, my red flag warning went up right there. You should NEVER enable macros unless you completely trust the sender and the legitimacy of the document. Even then, you should be extremely careful!
Opening the attachment
Since I am on a Mac, I decided to actually open the document. I wouldn’t recommend this on a Windows machine. And I probably wouldn’t recommend it on a Mac either. But I wanted to learn more.
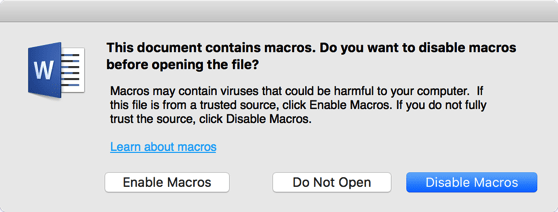
When I launched Microsoft Word, I was given the following warning:
This prompt will appear on both Windows and Mac versions of Microsoft Office. It is there to protect you so pay attention to that.
I clicked the “Disable Macros” button which is the default. This would obviously disable the macros but also allow me to view the macros.
Viewing the Malicious Word Macros
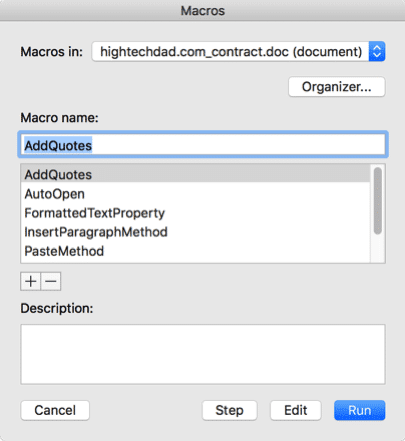
Once I had the Word doc open, I decided to take a look at the various macros within it. Be careful never to run a macro, just view them. In Microsoft Word for the Mac, you can access the macros from the View > Macros menu.
Once I did that, I could seen there were a variety of macros within the document. Some looked legitimate in the first set of macros:
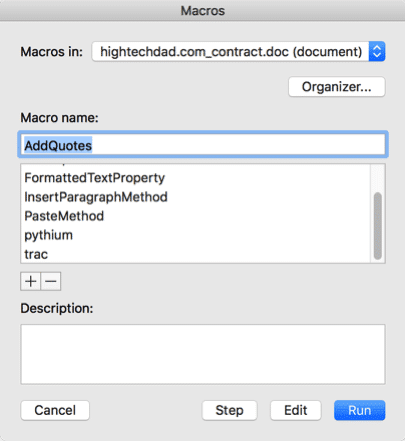
But scrolling down the list, I found some that looked like malicious Word macros:
Specifically, “pythium” and “trac” looked odd to me.
DON’T CLICK RUN! Click Edit instead if you want to view them.
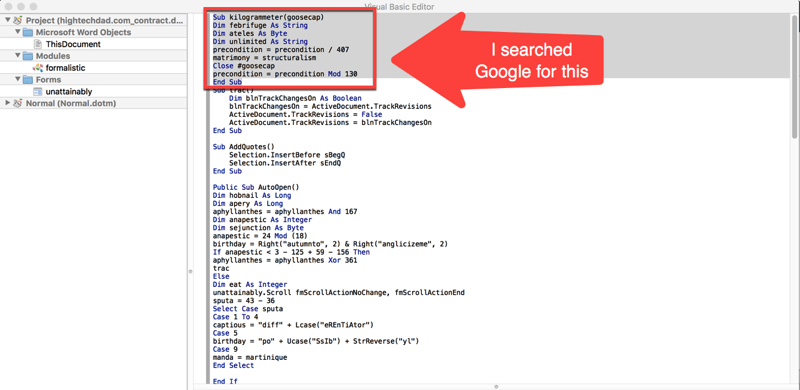
Clicking on the Edit button brought up what to me looked like pretty complicated macro code. I normally can get a basic understanding of what a macro does because I have created some myself in the past. These looked very cryptic.
Below is a sample of the beginning of the malicious Word macro code.
Since I couldn’t understand what the macro was trying to do (I’m not a coder), I decided one way was to actually search for some of the lines of the macro itself. So you can see the lines I searched for highlighted above.
Malicious Word macros search & analysis results
I was actually happily surprised to find that my search actually produced some good results. And, on top of that, I discovered a very helpful free service that lets you analyze documents for viruses or malware.
The site is called Reverse.it and is provided by a company called Payload Security. There is another domain it uses called hybrid-analysis.com. All three of these are the same service which basically is an automated malware analysis system which runs protected virtual environments and sandboxes to analyze documents for threats. (Note: I have no affiliation with this company.)
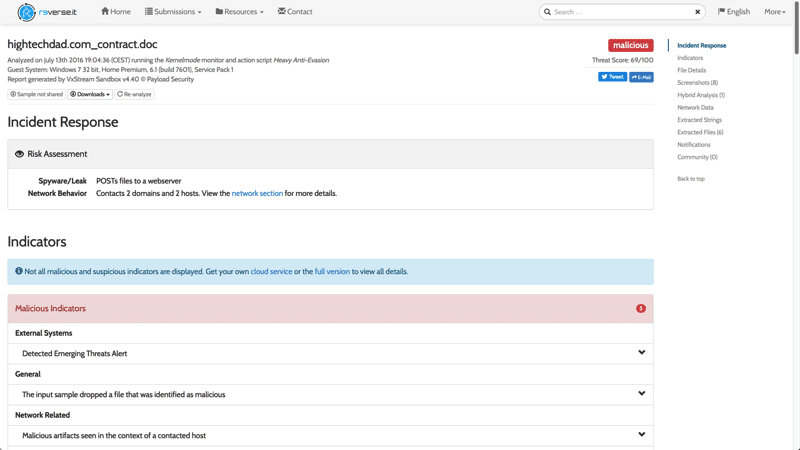
So I uploaded the attachment for analysis and within a few minutes received a tremendously intricate report of the analysis. Below is the top section of the results.
Just from reading the top portion, I knew the file was bad. It was flagged as “malicious” and had a threat score of 69/100. It was noted as a “Spyware/leak – POSTs files to a webserver” and “Network Behavior – Contacts 2 domains and 2 hosts”. That basically means that this malicious Word macro will upload your files to some foreign server somewhere. YOW!
That alone made me realize it was important for me to share this malicious Word macro warning.
If you want to see the Full Analysis of the file I received, you can view it here.
Also, I did a search of the Payload Security service for files that contained “_contract.doc” that were analyzed by there service and there were two pages of results. So, this particular malicious Word macro malware has been out there for a while, I’m guessing.
But if you have files you are concerned about that you have received as attachments, you can upload them to this service to see if they are dangerous or not.
The bottom line
There are lots of threats out there, especially in the form of legitimate looking emails and attachments. If you don’t know the sender, don’t open the attachment. If you aren’t expecting an attachment, don’t open it. If you don’t have anti-virus software, get some. If you received a message from your financial institution, don’t click on the link (go to the site directly instead). You get the picture. Be overly cautious.
HTD says: It is critical to be extremely cautious when it comes to digital files, email and your day-to-day activity. Just slow down and be careful!


1 comment
Jaime D
What if I already opened and clicked enable!?!?!!? Realized the second I pressed it, this was malicious… UGH!?!?!?